 FIDO2 keys as a security method is available with Microsoft Azure AD for already a couple of years now. Being the most secure access method available for Office 365 user access, enrolling FIDO2 security keys had a requirement of MFA to be configured for the users, which made it useless for use cases where users do not have (or do not want) to use multiple devices to log in. This has finally changed!
FIDO2 keys as a security method is available with Microsoft Azure AD for already a couple of years now. Being the most secure access method available for Office 365 user access, enrolling FIDO2 security keys had a requirement of MFA to be configured for the users, which made it useless for use cases where users do not have (or do not want) to use multiple devices to log in. This has finally changed!
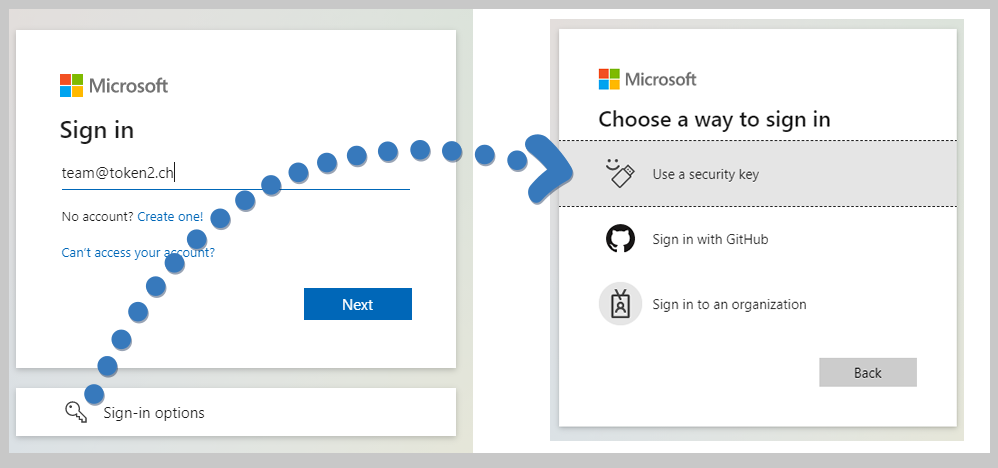
During the MS Ignite 2021 conference (which was held virtually this year as well), in addition to GA of Passwordless, Microsoft also announced a new feature, Temporary Access Pass in Azure AD (Preview), which will allow your end users to use only a FIDO2 Security key to access their account (this eliminates the requirement of having the MFA configured prior to that, which was the case before).
The guide below will describe how the administrator can set Temporary Access Pass for a user, and how that user can subsequently enroll his/her FIDO2 security key
Configure Azure Passwordless without MFA requirement
integration guides

Did you know?
Token2 is offering currently the most secure FIDO2 keys for enterprise customers, known as the PIN+ Series FIDO2 keys. These keys, certified by the FIDO alliance, enforce PIN complexity at the firmware level. This unique feature is not available with other keys, even those marked as FIPS-certified.Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
