OAuth2- TOTPRadius VPN Portal - Easy and secure access to corporate VPN
Starting from v0.2.5 TOTPRadius provides new ways of connecting to your corporate VPN systems based on L2TP, such as Meraki Client VPN or Fortinet VPN . The new web-based VPN portal allows logging in using additional methods, such as FIDO Security keys, both in Passwodless mode (if FIDO2 keys are used) and using the keys as the second factor (allowing to use legacy U2F FIDO hardware), as well as Azure AD (Microsoft Entra ID) SSO via OAuth2 protocol. VPN entries require no special VPN client, although T2VPN connection helper apps are recommended to minimize user actions. The VPN interface is based on a web server running on the same appliance as the TOTPRadius administration portal, but using a different port. This is done to isolate the administrative portal from the public internet facing user portal. As a general recommendation, the administrative web portal should be accessible only inside the network and protected by the firewall rules, limiting web and ssh access to IP addresses inside the network belonging to administrators' machines and RADIUS port (UDP 1812) to the VPN appliance only.
Demo
The video below show the user experience when using Oauth2 VPN portal. There is no user login procedure shown as the user account used in this demo has already logged on to Office 365 web interface, therefore SSO is used.
The network setup and required firewall rules for different usage modes of TOTPRadius are described in this article. It is also important to set-up an FQDN and HTTPS web certificate for the VPN Web portal.
This guide describes how to configure TOTPRadius VPN Web portal as an OAuth Resource and Azure AD (Microsoft Entra ID) as an External OAuth Authorization Server to facilitate secure access to the VPN resources connected to TOTPRadius. Important to mention that the account security in this configuration mode fully relies on Azure AD (Microsoft Entra ID) Configuration, therefore it is highly recommended that you have MFA or Passwordless enabled for accounts allowed to access this resource.
Configure the OAuth Resource in Azure AD (Microsoft Entra ID)
1. Navigate to the Microsoft Azure Portal and authenticate.
2. Navigate to Azure Active Directory.
3. Click on App Registrations.
4. Click on New Registration.
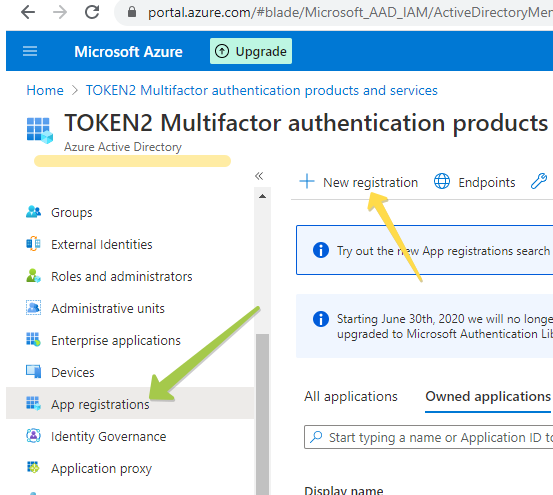
In the New Registration dialog, fill the form as shown on the example below, and click on “Register” to complete the action
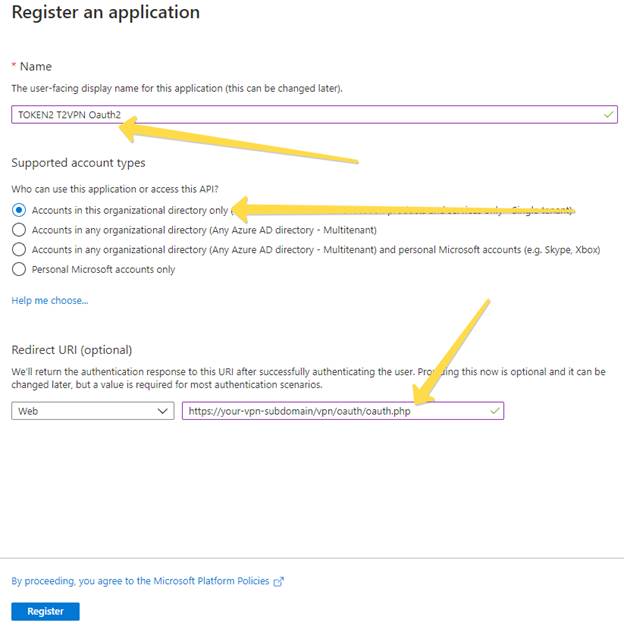
After the App Registration is done, the Overview of the object will be shown (see example below).
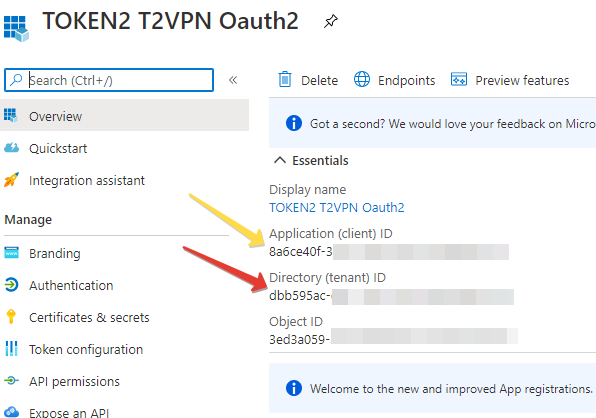
Note down the 2 IDs shown on this page (this can be retrieved at a later stage as well):
- Application (client) ID
- Directory (tenant) ID
These values will be entered later into the TOTPRadius configuration settings.
In the next step we will create a Client secret.
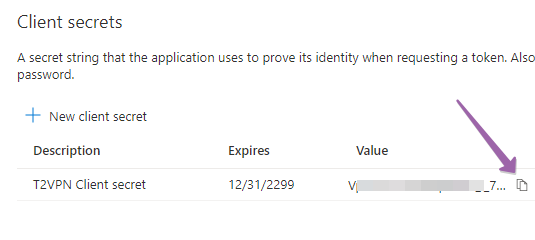
1. Click on Certificates & secrets and then New client secret.
2. Add a description of the secret.
3. Select never expire. For testing purposes, select secrets that never expire.
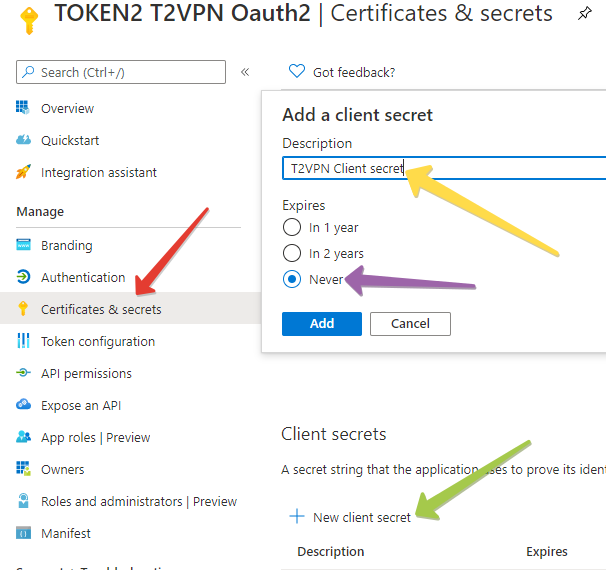
After the Client secret is created, copy its value and note down. This will also be used in TOTPRadius configuration.
Configure the OAuth2 Settings in TOTPRadius
Log in to TOTPRadius admin portal and navigate to General Settings section. Scroll down to Oauth2 VPN Portal settings section and fill the values as illustrated below:
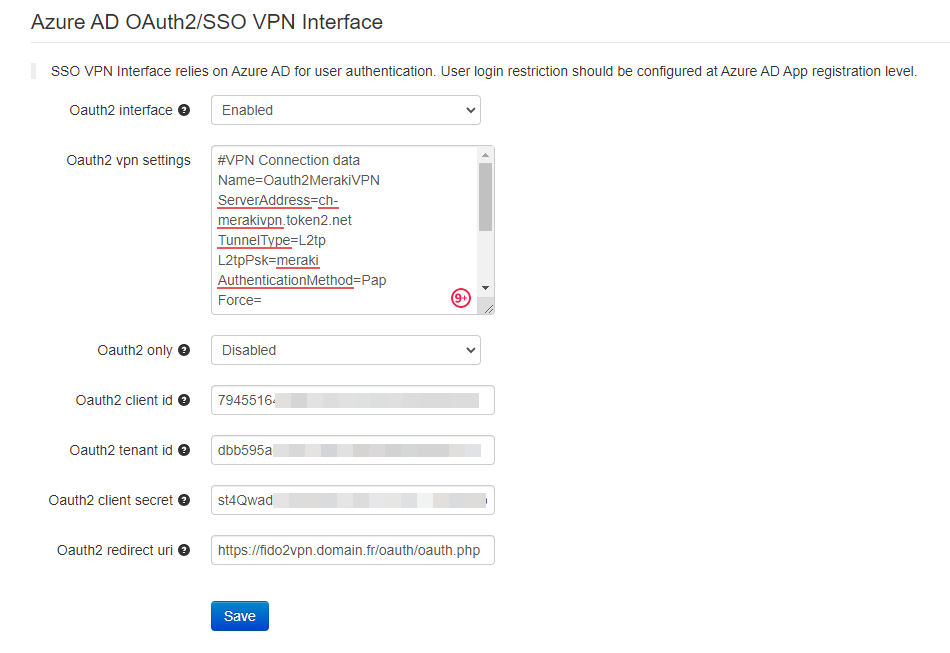
The settings shown on this example are explained in the table below:
|
Setting |
Description and possible values |
|
Oauth2 interface |
Enable or disables Azure AD (Microsoft Entra ID) Oauth2 SSO interface for VPN Portal |
|
Oauth2 VPN settings |
A configuration file template used to generate the connection files. The one on the screenshot above is showing the connectivity for Meraki Client VPN |
|
Oauth2 only |
If this setting is enabled, TOTP-based VPN access will be denied. Please note that this does not restrict FIDO2 login functionality (it has to be controlled separately) |
|
Oauth2 client id |
Client ID as recorded when creating App Registration with Azure |
|
Oauth2 tenant id |
Tenant ID as recorded when creating App Registration with Azure |
|
Oauth2 client secret |
Client Secret as recorded when creating App Registration with Azure |
|
Oauth2 redirect URI |
The URL of oauth.php script. Should match the URL specified in App Registration |
Once the settings are configured, you can test by visiting the configured FQDN. The OAuth2 interface is located in "oauth" folder (i.e. https://vpn-portal-fqdn/oauth/index.php)
User restrictions
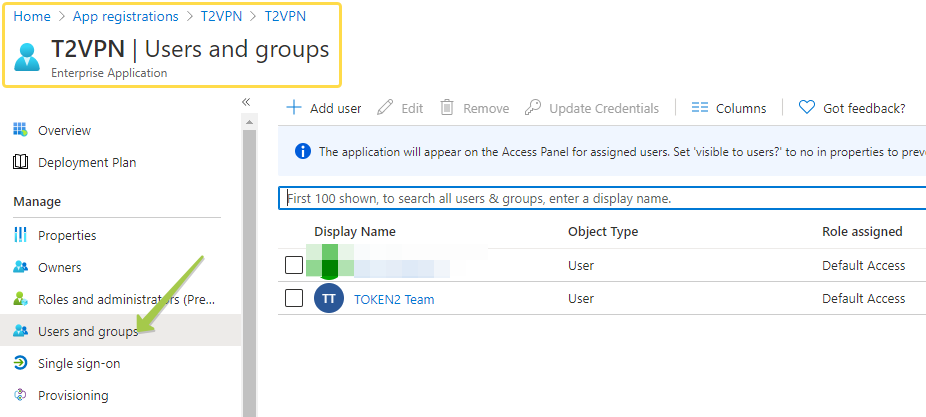
As mentioned before, restricting users to access the OAuth2 VPN portal can be done via Azure AD (Microsoft Entra ID) App Registrations settings. The Users and Groups settings are located in a different interface and can be accessed by clicking on the App's link under "Managed application in local directory"
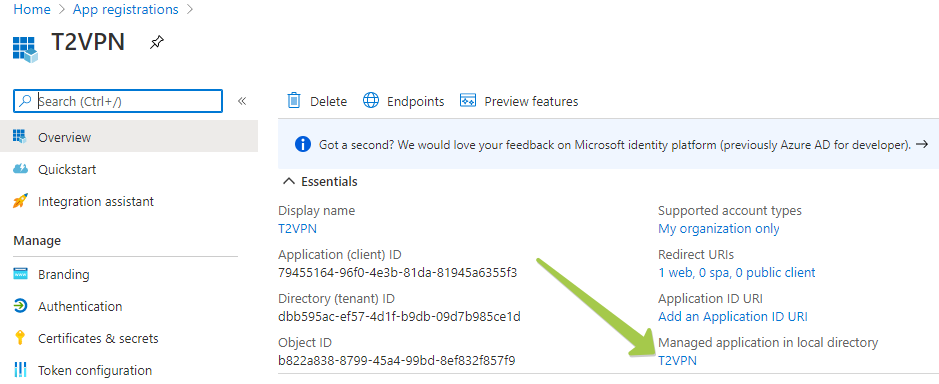
Navigate to Properties, then set "User assignment required?" to "Yes"
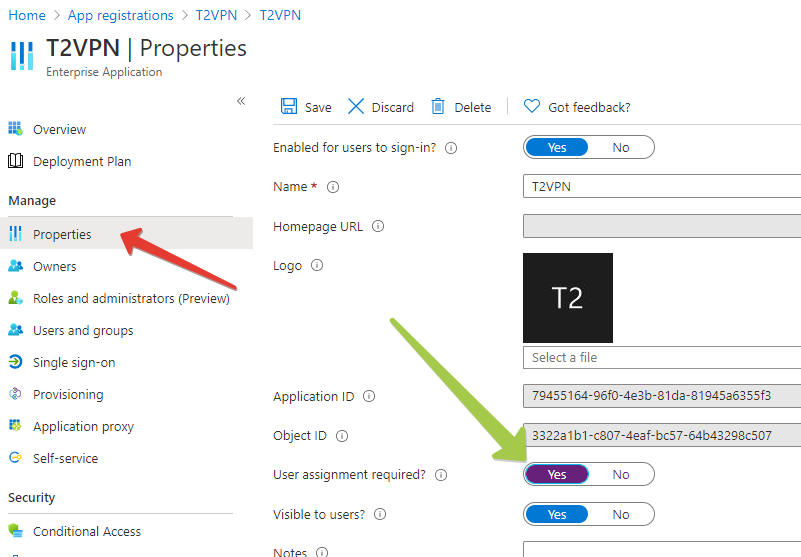
From the Application management interface, choose Users and Groups and add the users allowed to access this interface. Please note that groups are only available for assignment with Azure AD (Microsoft Entra ID) Premium P2 or EM+S E5 Licenses. With lower plans you can assign individual users to the application.
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
16-09-2025
Token2 PIN+ Keys Now Supported by MojeID at High Assurance Level
 MojeID, the Czech national digital identity service operated by CZ.NIC, has officially added Token2 PIN+ security keys to its list of devices accepted for the high assurance (úroveň záruky vysoká) level.
MojeID, the Czech national digital identity service operated by CZ.NIC, has officially added Token2 PIN+ security keys to its list of devices accepted for the high assurance (úroveň záruky vysoká) level.
