TOTPRadius - RADIUS Dynamic attribute response based on AD Group membership
This can be configured in Settings → RADIUS Service configuration:
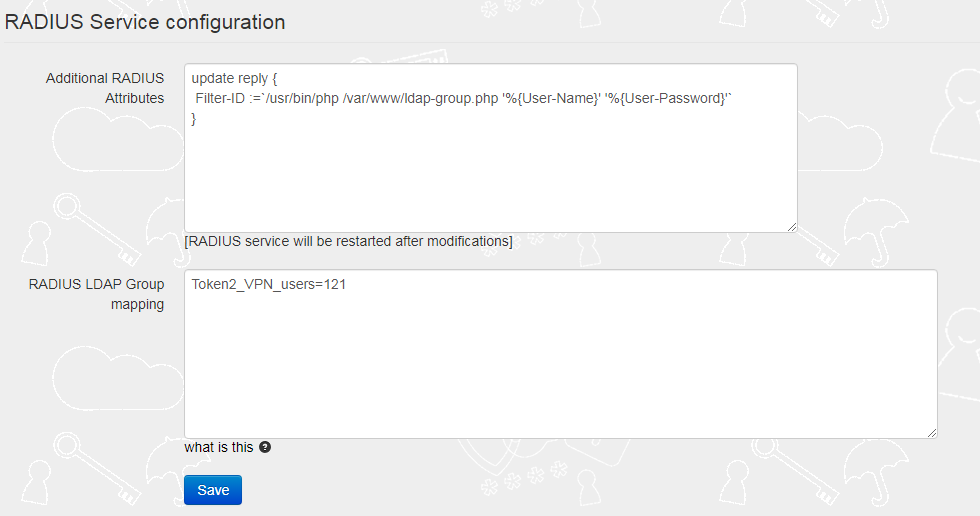
The 'Additional RADIUS Attributes' field should contain the reference to the ldap-group script as shown on the example below:
update reply { Filter-ID :=`/usr/bin/php /var/www/ldap-group.php '%{User-Name}' '%{User-Password}'` }
Important: The group names used for this parameter should not contain "=" sign.
The 'RADIUS LDAP Group mapping' field should contain a mapping rule, which allows members of the specified AD group to have Tunnel-Private-Group-ID attribute equal to some value.
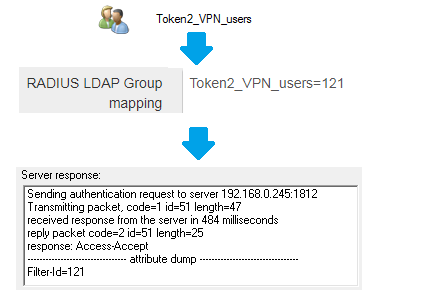
For the example above, if a user belongs to an AD Group named 'Token2_VPN_users', the Filter-ID will be included in the Radius reply as below:
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
16-09-2025
Token2 PIN+ Keys Now Supported by MojeID at High Assurance Level
 MojeID, the Czech national digital identity service operated by CZ.NIC, has officially added Token2 PIN+ security keys to its list of devices accepted for the high assurance (úroveň záruky vysoká) level.
MojeID, the Czech national digital identity service operated by CZ.NIC, has officially added Token2 PIN+ security keys to its list of devices accepted for the high assurance (úroveň záruky vysoká) level.
