Using Token2 Security keys for Silverfort
 Silverfort offers a unified identity protection platform that consolidates security controls across corporate networks and cloud environments to effectively block identity-based attacks.
Utilizing agentless and proxyless technology, Silverfort seamlessly integrates with all existing IAM solutions—including AD, ADFS, RADIUS, Azure AD (Microsoft Entra ID), Okta, Ping, and AWS IAM—extending their coverage to assets such as homegrown and legacy applications, IT infrastructure, file systems, command-line tools, machine-to-machine access, and more.
Silverfort also extends MFA to any sensitive resource, including those that were previously unprotected.
Silverfort offers a unified identity protection platform that consolidates security controls across corporate networks and cloud environments to effectively block identity-based attacks.
Utilizing agentless and proxyless technology, Silverfort seamlessly integrates with all existing IAM solutions—including AD, ADFS, RADIUS, Azure AD (Microsoft Entra ID), Okta, Ping, and AWS IAM—extending their coverage to assets such as homegrown and legacy applications, IT infrastructure, file systems, command-line tools, machine-to-machine access, and more.
Silverfort also extends MFA to any sensitive resource, including those that were previously unprotected.You can configure a FIDO2 service in Silverfort to support FIDO2 tokens for either a cloud-based service or an on-premises service, which is ideal for deployments with limited or no access to the cloud. In this guide, we will outline the steps needed to configure Token2 Security keys as a FIDO2 authentication method for two-step verification.
Requirements:
• An access to the Silverfort admin console.• Admin access to enable security keys (not required if security keys are already enabled)
• Modern browser supporting security keys.
• A Token2 FIDO security key.
• Silverfort Desktop App or the Silverfort Chrome extension to approve MFA requests.
Enable an MFA method
You can configure a FIDO2 service in Silverfort, to support FIDO2 tokens. You can configure a cloud-based service, or an on-prem service (for deployments with limited or no access to the cloud.Follow these steps to configure a FIDO2 service, either cloud-based, or an on-prem.1. On the 'SETTINGS' page, select 'MFA Tokens,' and then click on the 'On-prem FIDO2' tab.
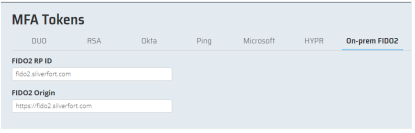
2. Set the FIDO2 RP ID and FIDO2 Origin settings based on whether your configuration is cloud-based or on-premises.
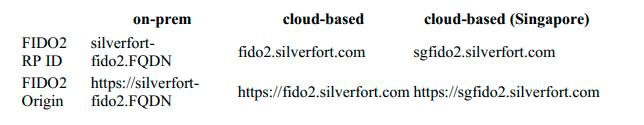
Where 'silverfort-fido2' resolves to the Admin Console.
3. To register a FIDO2 key, open the address 'https://FiDO2 Origin/register' in a browser. For example, for an on-premises service, this would be 'https://silverfort-fido2.FQDN', while for cloud-based services, you can use either 'https://fido2.silverfort.com/register' or 'https://sgfido2.silverfort.com/register'.
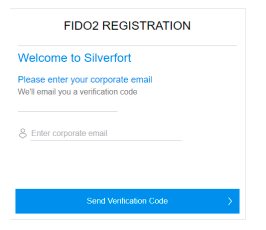
4. Enter your email address, then click 'Send Verification Code.' This email is used to identify the user associated with the token.
NOTE: You can register a FIDO2 token using an external email address only for the on-prem FIDO2 option. For the cloud-based option, the email must be in the AD.
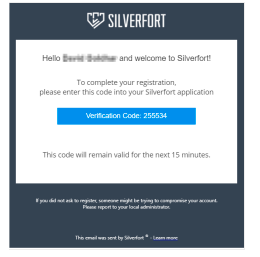
5. Check your email for a message like this and copy the verification code.
6. Insert your FIDO2 key and touch it. This action will generate a unique public and private key for the token, enabling its use.
Use FIDO2 tokens in Silverfort authentication policies
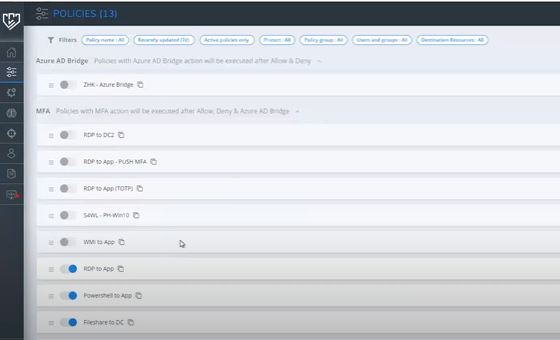
After enrolling the security key, we need to assign FIDO2 to Silverfort authentication policies. When a user in the policy attempts to access a resource, a message will be displayed in the Desktop App or Chrome extension, prompting them to approve the MFA using their token.1. In the POLICIES page, edit the settings for existing policy.
2. Go to the 'Action' section, select 'MFA'.Then assign 'FIDO2' to the 'Tokens' parameter.
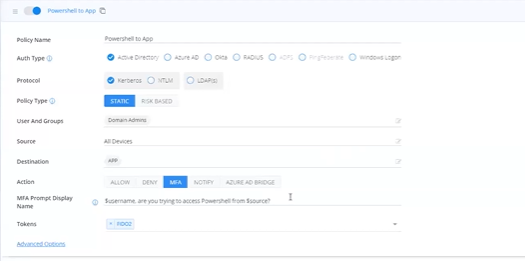
3. Specify the 'MFA Prompt Display Name' template as the message displayed in the Desktop App or Chrome extension.
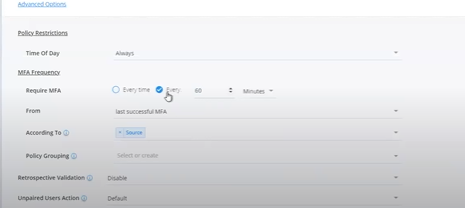
4. In the 'Advanced options,' choose a value for 'Require MFA': either every time or after a certain duration.
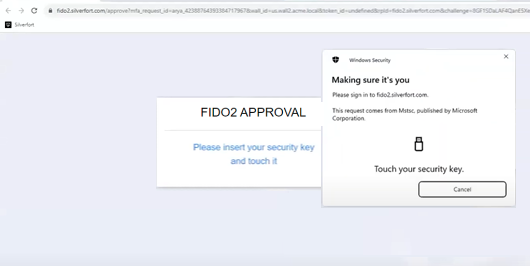
Now, when the policy is in effect, you will see a window in the notification area like the one below.
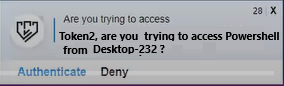
Insert the FIDO2 key and click 'Authenticate'. You will then be redirected to the Silverfort authentication page.
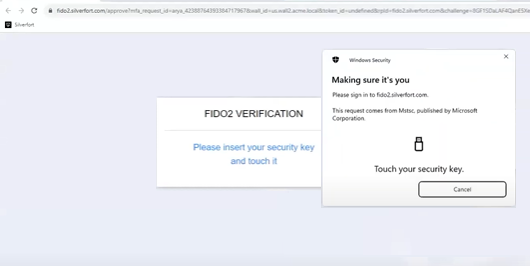
Touch the key to continue, and you will successfully gain access to the resource.
Key Benefits
Extend Token2 FIDO2 MFA Everywhere
Secure access to all resources, on-prem or in the cloud, including those that could not be protected until now.
Advanced Risk Analysis
Evaluate the risk of each access attempt based on the user’s full context.
Real-Time Protection
Detect and prevent advanced identity-based attacks across your entire environment.
Consistent User Experience
Provide users with a single MFA solution when requesting access to any resource, on-prem or on the cloud.
No MFA Fatigue
Ensure users are required to respond to an MFA only when Silverfort’s risk engine detects irregular activity
visit silverfort.com for more information
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
